This post is a deep dive into what happens in Nova (and where in the code) when a console URL is retrieved via the nova API for a Nova configuration backed by XVP and XenServer/XenAPI. Hopefully the methods used in Nova’s code will not change over time, and this guide will remain good starting point.
Example nova client call:
[code]nova get-vnc-console [uuid] xvpvnc[/code]
And the call returns:
+--------+-------------------------------------------------------------------------------------------------------+
| Type | Url |
+--------+-------------------------------------------------------------------------------------------------------+
| xvpvnc | https://URL:PORT/console?token=TOKEN |
+--------+-------------------------------------------------------------------------------------------------------+
One thing I particularly enjoy about console URL call in Nova is that it is synchronous and has to reach all the way down to the VM level. Most calls in Nova are asynchronus, so console is a wonderful test of your cloud’s plumbing. If the call takes over rpc_response/rpc_cast_timeout (60/30 sec respectively), a 500 will bubble up to the user.
It helps to understand how XenServer consoles work in general.
- XVP is an open source project which serves as a proxy to hypervisor console sessions. Interestingly enough, XVP is no longer used in Nova. The underpinnings of Console were changed in vnc-console-cleanup but the code is still around (console/xvp.py).
- A XenServer VM has a console attribute associated with it. Console is an object in XenAPI.
This Deep Dive has two major sections:
- Generation of the console URL
- Accessing the console URL
How is the console URL generated? 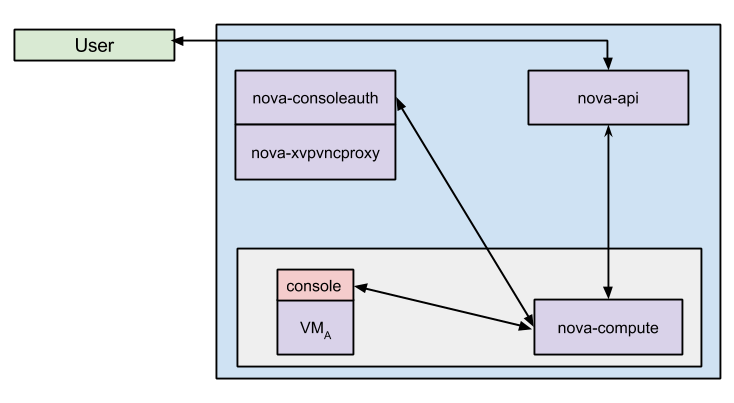 1) nova-api receives and validates the console request, and then makes a request to the compute API.
1) nova-api receives and validates the console request, and then makes a request to the compute API.
- api/openstack/compute/contrib/consoles.py
- def get_vnc_console
- The compute RPC API receives the request and does two things: (2a) calls compute RPC API to gather connection information and (2b) call the console authentication service.
- compute/api.py
- def get_vnc_console
2a) The compute RPC receives the call from (1). An authentication token is generated. For XVP consoles, a URL is generated which has FLAGS.xvpvncproxy_base_url and the generated token. driver.get_vnc_console is called.
- compute/manager.py
- def get_vnc_console
2a1) driver is an abstraction to the configured virt library, xenapi in this case. This just calls vmops get_vnc_console. XenAPI information is retrieved about the instance. The local to the hypervisor Xen Console URL generated and returned.
- virt/xenapi/driver.py
- def get_vnc_console
- virt/xenapi/vmops.py
- def get_vnc_console
2b) Taking the details from 2a1, the consoleauth RPC api is called. The token generated in (2a1) is added to memcache with CONF.console_token_ttl.
- consoleauth/manager.py
- def authorize_console
What happens when the console URL is accessed? 
- The request reaches nova-xvpvncproxy and a call to validate the token is made on the Console Auth RPC API
- vnc/xvp_proxy.py
- def __call__
- The token in the request is checked against the token from the previous section (2b). Compute’s RPC API is called to validate the console’s port against the token’s port.
- consoleauth/manager.py
- def check_token
- def _validate_token
- compute/manager.py
- def validate_console_port
- nova-xvpvnc proxies a connection to the console on the hypervisor.
- vnc/xvp_proxy.py
- def proxy_connection